ASIS Hawaii Chapter 134
Chartered on September 21, 1980
General Membership Meetings
You are cordially invited to attend our General Membership Meetings that are held in person at the HIDTA-Hawaii Conference Room. Please refer to our ASIS 2026 Calendar for dates and times and email us for the exact location. We can also share a ZOOM link if you would like to attend virtually. Aloha!

Mahalo to Our Supporters and Sponsors!
On behalf of ASIS International Hawaii Chapter, we extend our deepest gratitude to all our supporters and sponsors who made the ASIS Golf Tournament a resounding success! Your generosity and commitment played a vital role in supporting our mission.
Thank you for being a part of our journey.
Supporting Students
in pursuit of a
Criminal Justice
Degree*
2025 GOLF
TOURNAMENT
Friday, April 4, 2025


NEWS
David K. Porter

FBI Honolulu Special Agent in Charge David K. Porter was the featured guest speaker at our January 2026 ASIS Hawai‘i Chapter meeting, where he shared his perspectives on the FBI’s mission in Hawai‘i and outlined key priorities guiding the Bureau’s work in our community. Pictured here (from left): FBI Honolulu SAC Porter,Debra Allen, ASIS Member and Managing Agent of 808 Investigations, LLC, and Robert Cravalho, PCI, Secretary of the ASIS Hawai‘i Chapter. A special mahalo to Debra for generously sponsoring the meeting lunch and supporting the Chapter.
Bev Baligad, JD

Bev Baligad, JD, Director of Compliance at the University of Hawai‘i – West O‘ahu, was our featured guest speaker at the November ASIS Hawai‘i Chapter meeting. She delivered an engaging and informative presentation on threat assessment and management, offering valuable insights for security professionals across our community. Pictured here (from left): ASIS Hawai‘i Chapter Chair Jerry Pahukula, Jr., CPP, First Hawaiian Bank, Bev Baligad, JD, and ASIS Hawai‘i Chapter Vice Chair Ed Howard, Pax Bello Security Solutions Hawaii, LLC. A special mahalo to Hawaiian Island Investigations, LLC for generously sponsoring our meeting lunch. If you would like to sponsor our next meeting lunch, just click on the link SPONSOR LUNCH on the Home Page.
Dr. David Haymer

Dr. David Haymer, Professor of Genetics at the University of Hawai‘i at Mānoa, John A. Burns School of Medicine, was our featured guest speaker at our September meeting. He shared his expertise on the use of DNA across various fields, including forensic science, research, and efforts to correct wrongful convictions. Dr. Haymer is pictured here with ASIS Hawaii Chapter Chair Jerry Pahukula, CPP. Additionally, we thank First Hawaiian Bank for sponsoring our meeting lunch.
Director Mike Lambert

Director Mike Lambert of the State of Hawaii Department of Law Enforcement was our featured guest speaker at our June meeting. He shared exciting plans to enhance safety in Waikīkī through the use of advanced technology. We extend our sincere thanks to Director Lambert for his leadership and vision, and to Rick Osborne from EverOn for generously sponsoring our lunch. Director Lambert is pictured here with ASIS Hawaii Chapter Chair Jerry Pahukula, CPP.
MR. Joseph Aguon, CPP

MR. Joseph Aguon, CPP, joined us as the guest speaker for our February meeting, sharing valuable insights on the use of Artificial Intelligence (AI) in the workplace. He highlighted the advantages of AI for generating letters, emails, and reports while also addressing important legal and privacy concerns. Joe emphasized the importance of companies implementing AI policies as a proactive measure. Chair Jerry Pahukula, CPP, presented Joe with our Certificate of Aloha and a SWAG Bag as a token of appreciation. Mahalo, Joe! A special thank you to Frank Untulan, Dr. Jennifer Borja-Johnson, and Securitas for generously sponsoring lunch for the event. Interested in sponsoring our next lunch? Click the SPONSOR LUNCH button on the left side of this page!
Chief Arthur 'Joe' Logan

Honolulu Police Chief Arthur 'Joe' Logan joined us as the guest speaker at our January meeting, where he shared his key priorities for the police department: Recruiting, Reducing Crime, and Creating Culture. Chief Logan also addressed topics like ghost guns and the approval of specific equipment for security officers. Pictured here with Chief Logan is our Chair, Jerry Pahukula, CPP. We extend our heartfelt thanks to Ed Howard, President and CEO of Pax Bello Security Solutions Hawaii, LLC., for generously sponsoring lunch for the event.
Joe Cabrejos, CII

Joe Cabrejos, CII, was our guest speaker at the November meeting, where he provided valuable insights into Open-Source Intelligence (OSINT). As a private investigator, Mr. Cabrejos utilizes OSINT to track and identify individuals and gather critical intelligence. He is pictured here with Vice Chair Ed Howard, CHPP. We also extend our gratitude to Christine Lanning, President of Integrated Security Technologies, Inc., for generously sponsoring our lunch at the event.
Bev Baligad, JD

Ms. Bev Baligad, JD, was our guest speaker at the September meeting. As the Director of Compliance at UH West O‘ahu and Chair of Threat Team Hawaii (TTH), she shared TTH’s mission, how to access their support, and ways to join the General Stakeholder group. For more information, you can contact TTH through the Hawaii Fusion Center.
Steve Alm, Honolulu Prosecuting Attorney

Honolulu Prosecuting Attorney Steve Alm was our guest speaker at the August meeting. Many of you may remember him from his impactful tenure as a Honolulu Circuit Court Judge, where he pioneered the nationally recognized HOPE Probation program. During the meeting, he gave us an insightful overview of the Department of the Prosecuting Attorney, highlighting both the achievements and ongoing efforts of his office. Thank you, Judge Alm, for your time and for sharing your leadership with Honolulu!
Gary Yabuta, Executive Director, Hawaii-HIDTA
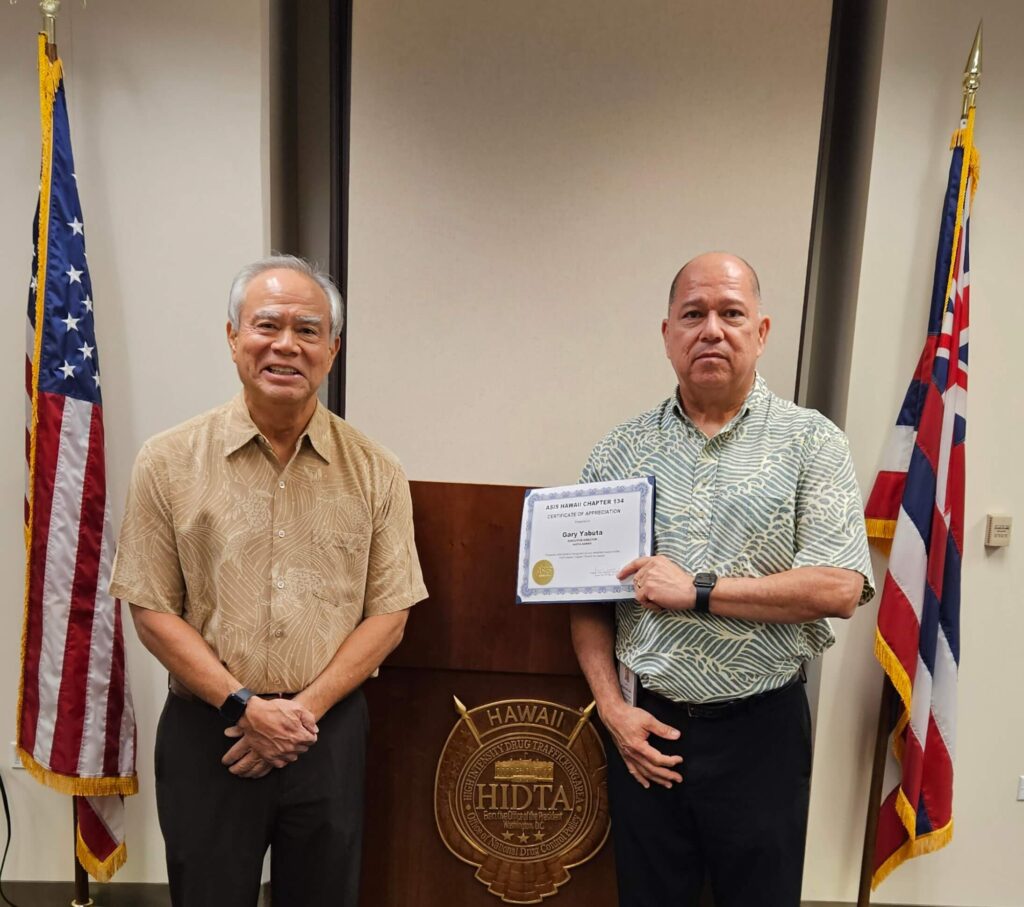
Director Yabuta, who previously served as the Maui County Chief of Police, is now leading HIDTA Hawaii. He shared the history and mission of the 33 HIDTAs across the country and discussed the challenges of controlling the import of illegal narcotics into our island home. Thank you, Director Yabuta, for serving as our guest speaker and educating us.
ASIS Hawaii 2023 Holiday Party at Buca di Beppo, Ward Entertainment Center
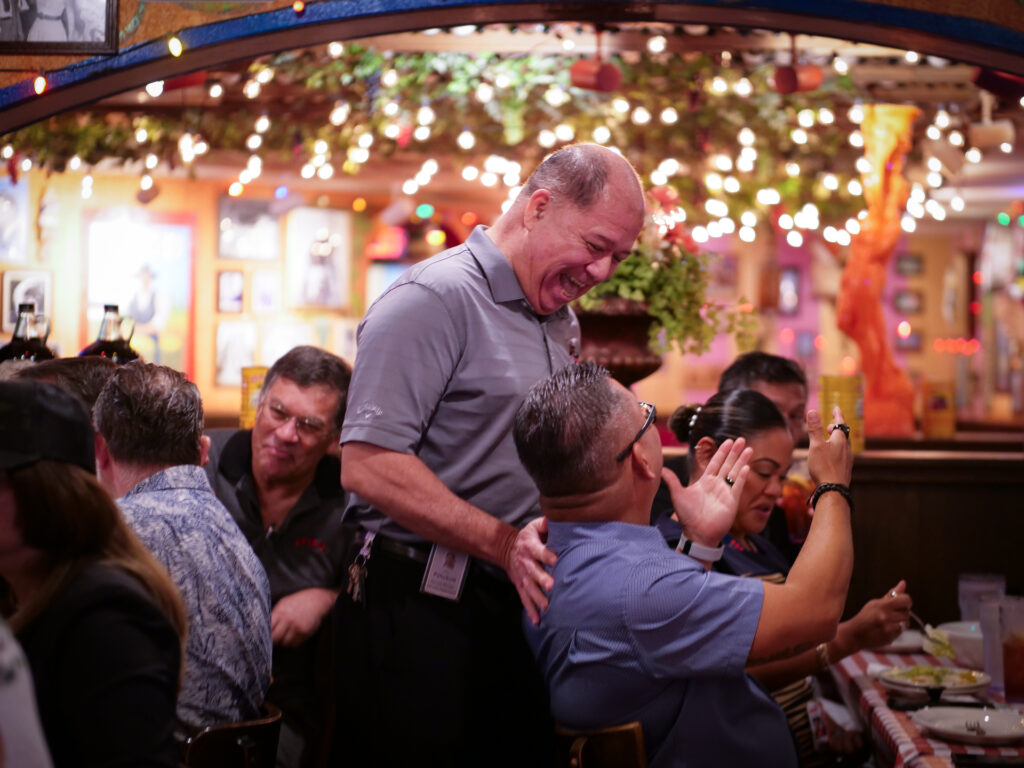
The ASIS Hawaii Chapter invites you to attend their Holiday Party where we will install our new leaders for 2024! There will be food, fun and fellowship to share. Holiday give-a-ways too!
Ken Nakamura, Threat Assessment Detective, City of Roseville

Ken Nakamura was the guest speaker at our August 2022 virtual membership meeting. Outside of being a police detective, Ken is a member of: Association of Threat Assessment Professionals; ASIS International; and the U.S. CEPTED (Crime Prevention Through Environmental Design) Association.
Ken’s presentation “Threat Assessment and Threat Management” included a real case study that truly enhanced the talking points of his material. The case study was riveting.
Thank you very much Ken.
Wayne Parker, Director of Law Enforcement Controlled F.O.R.C.E.

Wayne Parker from Controlled FORCE, was the guest speaker at out July 2022 virtual membership meeting. Wayne’s presentation on “De-Escalation for First Responders” was very informative. I wish we could have given him more time. Thank you Wayne.
Mike Petty, Thermal Imaging Radar, LLC

Mike Petty, VP of Sales at Thermal Imaging Radar, LLC and Trustee for the ASIS Foundation Board was the guest speaker at our June 2022 virtual membership meeting. Mike provided an informative briefing on the ASIS International Foundation and discussed “Persistent Intrusion Detection Methods.
Dave Weiner, Secure Measures, LLC

In May 2022 we were pleased to have Mr. Dave Weiner, Founder and CEO of Secure Measures, LLC, as our guest speaker. Dave has served in the military, law enforcement and corporate security for 27 years and discussed a number of topics related to our veterans that may assist us when dealing with our veterans in the homeless community.
Joe Cabrejos, Goodenow Associates Investigations, LLC

Joe Cabrejos has been a career investigator since 1983 and is a partner and co-owner of Goodenow Associates Investigations, LLC. Regardless of the type of investigative assignments that Joe receives, they almost always begin with a foundational background investigation. With almost 40 years of experience in the investigative field, Joe shared his insight and experiences related to conducting background investigations.
Brent Tsuda, Shooter Detection Systems

Our March guest speaker Brent Tsuda, Director of Sales (West) at Shooter Detection Systems, made a very informative presentation on Active Shooter Detection Technology: from providing active shooter statistics to describing device technology and design requirements.
Ed Howard, Pax Bello Security Solutions Hawaii

In February 2022 our chapter’s own Ed Howard, Owner and CEO of Pax Bello Hawaii, discussed the new law (Hawaii Revised Statutes Chapter 134) regarding electric guns and what it means to the individuals of Hawaii.
Scott Spallina, Deputy Prosecuting Attorney

Scott Spallina, the Supervisor of the Elder Abuse Justice Unit was our guest speaker at our January 2022 virtual membership meeting. Scott established this unit in 2008 with the goal to “Enhance Awareness, Prevention, and Prosecution of Crimes Affecting the Elderly” in Hawaii. Scott’s presentation included statistical data, case stories, and red flags to be aware of.
December 2021 - ASIS Hawaii Christmas Party

Outgoing Hawaii Chapter Chair Jim Frame, CPP, received a Certificate of Aloha from the Chapter at their Holiday General Membership Meeting recognizing his 11 years of volunteer leadership to the organization. He is pictured with Chapter Treasurer Miguel Tostado, CPP, Assistant Regional Vice President Jerry Pahukula, CPP, and Chapter Secretary Robert Cravalho, PCI. Missing from the photograph is Chapter Vice Chair Christine Lanning, PSP.
June 2020 Meeting - How Has Covid-19 Affected Your Business Model
Security professionals, members of Hawaii 134 Chapter of ASIS International, discuss the implications of the Covid-19 situation on their businesses.
Rodney Hatanaka from ProTech Fire & Security

Rodney Hatanaka from ProTech Fire & Security was the guest speaker at our February 2020 meeting. He shared the different protocols and responses to electronic alarm systems.
Vice Chair Christine Lanning presented Rodney with a Certificate of Aloha for sharing his expertise with the membership.
Derek Chow, Deputy Director at Harbors Division, DOT

Derek Chow, Deputy Director at Harbors Division, Department of Transportation, State of Hawaii, was the keynote speaker at our January 2020 General Membership Meeting. He shared the importance of harbors to our economy and the exciting plans to expand on Oahu. Mr. Chow also outlined their challenges intercepting illegal fireworks at the docks.
Here, ASIS Hawaii Chair Jim Frame presents Mr. Chow with a Certificate of Appreciation for supporting the education of our members.
Russell Seeney, President of InfaGard Hawaii

Vice Chair Randall Mack presented Mr. Russell Seeney our Certificate of Appreciation at our November 13 General Membership Meeting. Mr. Seeney is the President of InfraGard Hawaii and provided valuable information about the organization.
Meeting with the Administrator for the Hawaii Emergency Management Agency
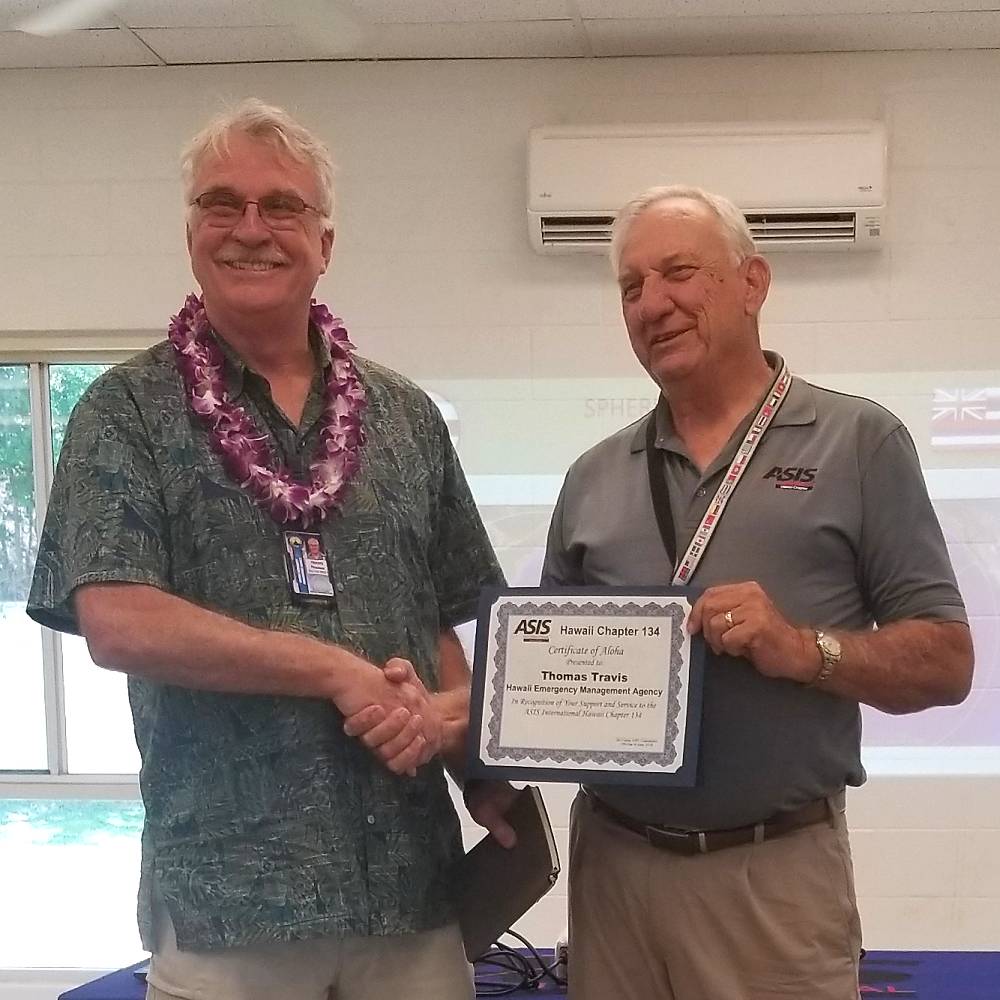
Mr. Thomas Travis, Administrator for the Hawaii Emergency Management Agency (HI-EMA), addressed our members on June 12, 2019. He spoke about resilience in emergency management.
Meeting with the Administrator for the Narcotics Enforcement Division

Our guest speaker for our May 2019 General Membership Meeting was Jared "Jerry" Redulla who is the Administrator for the Narcotics Enforcement Division, Department of Public Safety, State of Hawaii. He addressed the Hawaii's Opioid Addiction and provided an overview of the efforts to combat this national issue. Here, Jerry receives our Certificate of Aloha for visiting us.
Security Manager Nani Koa honored for Women Who Mean Business 2019

Nani Koa worked her way up through the ranks of Securitas Hawaii to become the only female branch manager in Hawaii. She was honored in March 2019 by Pacific Business News and was selected from a wide field of business women for the honor of Women Who Mean Business. Only 31 honorees were selected statewide.
Read more about her views on leadership in Pacific Business News.
“The security industry remains committed to the advancement of women,” says Jim Frame, ASIS Chairperson. “We encourage our partners and member companies to have women play a larger role in ASIS and other associations as well.”
Jonathan Baijo Discusses AEDs

Jonathan Baijo, Account Manager and Trainer from Safety Systems and Signs Hawaii, was our guest speaker at our March 2019 General Membership Meeting. Jon moderated a discussion on AEDs, that included a comparison on various models and upgrades to units.
Here, Chair Jim Frame (center) presents a Certificate of Aloha to Jon (left) as Jon's colleague Alan looks on (right).
Mike Johnson Talks about Frictionless Security and Trends

Mr. Mike Johnson, CPP, the Regional Sales Manager for Orion Entrance Control, Inc., was our guest speaker at the General Membership Meeting on Wednesday, February 13, 2019. Mike talked about Frictionless Security and Industry Trends. Here, Chairperson Jim Frame, CPP, presents Mike with a Certificate of Aloha for his support of our Hawaii Chapter.
Randy Mack, CPP receives Certificate of Appreciation

Chapter Vice President Randy Mack accepts Certificate of Appreciation from Chapter Chair Jim Frame at July 11th chapter meeting.
Jim Howe, Director of EMS Speaks to Chapter Members

Mr. Jim Howe, Director of Emergency Services for the City & County of Honolulu, receives a Certificate of Appreciation from Chapter 134 Chair Jim Frame.
Jim Howe provided an informational and insightful look at the current status of emergency health services in Honolulu.
FBI ASAC Tuan Nguyen Addresses Chapter

Chapter #134 Chair Jim Frame presents Certificate of Appreciation to FBI Assistant Special Agent in Charge Tuan Nguyen at the April 11th, 2018 meeting.
D.C. McCarthy Speaks on Cyber Crime

Mahalo to Deputy Chief John McCarthy who addressed our members at our March meeting. John discussed the ongoing threat of cyber crime and how it impacts us in both our personal and business lives. John is a strong supporter of ASIS and our chapter.
Police Chief Susan Ballard Addresses ASIS Chapter


Chapter members were honored to have Honolulu Police Chief Susan Ballard as our guest speaker. Chief Ballard spoke of her vision for the Honolulu Police department and focusing on the future of working together with organizations such as ours to improve the quality of life for all residents of Honolulu.

Chief Ballard responding to question from member Lana Rapoza.

Chief Ballard receiving Certificate of Appreciation from Chapter Chair Jim Frame.
Missile Alert - False Alarm
At 8:07am, January 13th, Hawaii State Warning Point issued a Missile Alert in ERROR. There was NO THREAT to the State of Hawaii.
Nominations for 2018 Executive Board
Nominations are now open for Chapter 134 executive board positions for 2018. The positions are Chapter Chair, Vice Chair, Treasurer and Secretary. Nominations can be emailed to [email protected] if you are interested in running or if you wish to nominate another member.
Nominations close at the meeting on November 8th and ballots will be emailed to members for voting.
Active Shooter Workshop
Several chapter members attended a Active Shooter workshop sponsored by the Department of Homeland Security at Blaisdell Center on Monday, June 26, 2017. This extremely informative workshop was brought to Honolulu by our local DHS Protective Security Advisor James Cruz. The all day workshop provided several modules on developing, planning and implementing an Active Shooter program for your company or agency. Additional information can be obtained by visiting the DHS website at http://dhs.gov and entering Active Shooter Workshop into the search box.
James is also available to answers questions and provide assistance to companies regarding DHS products and services that may be available to your organization. James is a great resource and I urge all members to utilize his skills.
City Launches New Emergency Notification Service
Effective June 1st, 2017, the City and County of Honolulu will discontinue sending emergency alert messages via the NIXLE notification system.
The city has developed its own emergency notification system and is available FREE via a mobile app from either the App Store or Google Play. Search for HNL.info. This app offers a free subscription to alerts and is able to be customized to the individual users preferences as to which alerts are received.
You can also register to receive email alerts at hnl.info/alerts/login.php

New ASIS PSP Exam 3Q Launch
ASIS Hawaii Chapter 134 Members:
Please be informed that the revised PSP exam, which originally had been scheduled to launch in March 2017 is now planned to launch in November 2017. To note, the 8-piece and newly consolidated 4-piece PSP reference material are both applicable for the current exam format. Test takers will not need to purchase new reference materials should they take the exam before November 2017.
If you have questions or require additional information, the certification team stands ready to assist. You can reach them at [email protected]
Top Cop Photos from 2016 LESAB
For pictures, visit https://topcophawaii.com/gallery-2016/
(180 pictures)
2017 Chapter Elections
2015 Uniform Crime Reports Released
FBI Releases 2015 Crime Statistics
After two years of decline, the estimated number of violent crimes in the nation increased 3.9 percent in 2015 when compared with 2014 data, according to FBI figures released today. Property crimes dropped 2.6 percent, marking the 13th straight year the collective estimates for these offenses declined.
The 2015 statistics show the estimated rate of violent crime was 372.6 offenses per 100,000 inhabitants, and the property crime rate was 2,487.0 offenses per 100,000 inhabitants. The violent crime rate rose 3.1 percent compared with the 2014 rate, and the property crime rate declined 3.4 percent.
These and additional data are presented in the 2015 edition of the FBI’s annual report Crime in the United States. This publication, which is a statistical compilation of offense, arrest, and police employee data reported by law enforcement agencies voluntarily participating in the FBI’s Uniform Crime Reporting (UCR) Program, also includes limited federal crime reporting, human trafficking, and cargo theft data.
The UCR Program collects information on crimes reported by law enforcement agencies regarding the violent crimes of murder and non-negligent manslaughter, rape, robbery, and aggravated assault, as well as the property crimes of burglary, larceny-theft, motor vehicle theft, and arson. (Although the FBI classifies arson as a property crime, it does not estimate arson data because of variations in the level of participation by the reporting agencies. Consequently, arson data are not included in the property crime estimate.) The program also collects arrest data for the offenses listed above plus 20 offenses that include all other crimes except traffic violations.
Prior to 2013, the FBI’s UCR Program collected rape data in the Summary Reporting System under the category “forcible rape.” In 2013, the program removed the term “forcible” from the title and revised the definition. The legacy UCR definition of rape is “The carnal knowledge of a female forcibly and against her will.” The revised UCR definition of rape is “Penetration, no matter how slight, of the vagina or anus with any body part or object, or oral penetration by a sex organ of another person, without the consent of the victim.”
Of the 18,439 city, county, university and college, state, tribal, and federal agencies eligible to participate in the UCR Program, 16,643 submitted data in 2015. A high-level summary of the statistics submitted, as well as estimates for those agencies that did not report, follows:
- In 2015, there were an estimated 1,197,704 violent crimes. Murder and non-negligent manslaughter increased 10.8 percent when compared with estimates from 2014.
- Rape and aggravated assault increased 6.3 percent and 4.6 percent, respectively, while robbery increased 1.4 percent.
- Nationwide, there were an estimated 7,993,631 property crimes. The estimated numbers for two of the three property crimes show declines when compared with the previous year’s estimates. Burglaries dropped 7.8 percent, and larceny-thefts declined 1.8 percent, but motor vehicle thefts rose 3.1 percent.
- Collectively, victims of property crimes (excluding arson) suffered losses estimated at $14.3 billion in 2015.
- The FBI estimated that law enforcement agencies nationwide made 10.8 million arrests, excluding traffic violations, in 2015.
- The arrest rate for violent crime was 157.2 per 100,000 inhabitants, and the arrest rate for property crime was 458.9 per 100,000 inhabitants.
- By violent crime offense, the arrest rate for murder and non-negligent manslaughter was 3.5 per 100,000 inhabitants; rape (aggregate total of revised and legacy), 7.1; robbery, 29.7; and aggravated assault, 117.0 per 100,000 inhabitants.
- By property crime offense, the arrest rate for burglary was 67.5 per 100,000 inhabitants; larceny-theft, 364.5; and motor vehicle theft, 24.2. The arrest rate for arson was 2.8 per 100,000 inhabitants.
- In 2015, there were 13,160 law enforcement agencies that reported their staffing levels to the FBI. These agencies reported that, as of October 31, 2015, they collectively employed 635,781 sworn officers and 277,380 civilians, a rate of 3.3 employees per 1,000 inhabitants.
Caution Against Ranking
Each year when Crime in the United States is published, some entities use the figures to compile rankings of cities and counties. These rough rankings provide no insight into the numerous variables that mold crime in a particular town, city, county, state, tribal area, or region. Consequently, they lead to simplistic and/or incomplete analyses that often create misleading perceptions adversely affecting communities and their residents. Valid assessments are possible only with careful study and analysis of the range of unique conditions affecting each local law enforcement jurisdiction. The data user is, therefore, cautioned against comparing statistical data of individual reporting units from cities, metropolitan areas, states, or colleges or universities solely on the basis of their population coverage or student enrollment.
Chapter member named to Advisory Commission
Congratulations to Chapter member Joe Miller who was recently appointed a Commissioner on the Civil Defense Advisory Commission of the Department of Emergency Management by Mayor Kirk Caldwell. Joe joins chapter member Jerry Dolak who is also currently serving as a Commissioner on the commission.
The Civil Defense Advisory Commission is established by Section 6-104, Revised Charter of the City and County of Honolulu to advise the mayor, the council and the director of emergency management on matters pertaining to civil defense, weather emergencies, emergency management and to promote community understanding and interest in such matters.
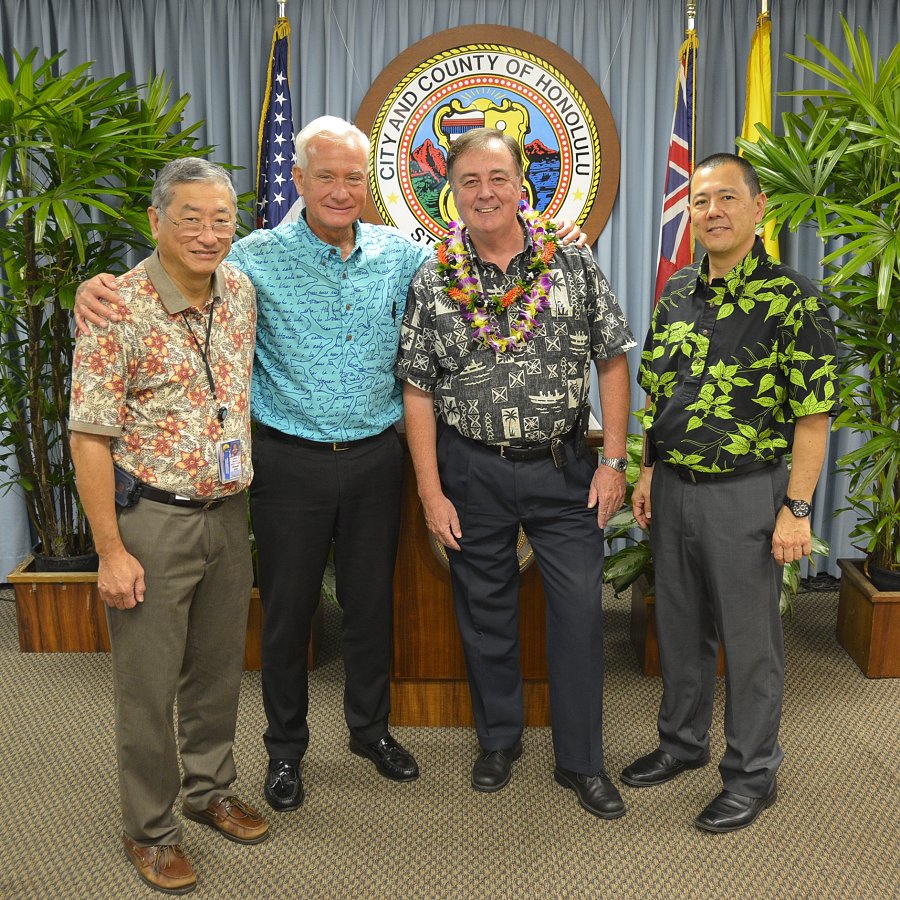
Left to right: Melvin Kaku, Director, Department of Emergency Management; Honolulu Mayor Kirk Caldwell, Joe Miller; Peter Hirai, Deputy Director, Department of Emergency Management
Annual Seminar 2016
Congratulations to Mr. Rick Osborne, PSP, who is this year's recipient of our annual Chapter 134 seminar ticket drawing.
Enjoy Orlando, the seminar and the exhibits!
Certification Update
Congratulations to chapter members Jerry Pahukula and Rick Osborne on earning their Physical Security Professional (PSP) certifications in July. Hard work, perserverance, and good study habits pay off!
New CPP Exam to Launch March 2016
CPP exam domains have been modified as a result of a worldwide analysis of security management jobs. Revised domains will be reflected in updated exams that will be administered beginning March 1, 2016.
If you plan to test before March 1, 2016, your exam will cover the domains as follows:
-
Security Principles and Practices (19%)
-
Business Principles and Practices (11%)
-
Investigations (10%)
-
Physical Security (25%)
-
Information Security (8%)
-
Crisis Management (8%)
-
Legal Aspects (7%)
Please note: If you are scheduled to test after February 29, 2016, you will be taking the updated exam. The exam has been revised and more information regarding the CPP certification is available on the ASIS International website at www.asisonline.org/certification. It is highly recommended to review this information thoroughly prior to taking the CPP exam. Following are the revised domains and their exam weights.
Updated Domains and Knowledge Statements
Domain I: Security Principles and Practices (21%) Old Weight (19%)
Task 01/01 Plan, develop, implement, and manage the organization’s security program to protect the organization’s assets
Knowledge of:
01/01/01 Principles of planning, organization, and control
01/01/02 Security theory, techniques, and processes
01/01/03 Security industry standards NEW
01/01/04 Continuous assessment and improvement processes NEW
01/01/05 Cross-functional organizational collaboration NEW
Task 01/02 Develop, manage, or conduct the security risk assessment process
Knowledge of:
01/02/01 Quantitative and qualitative risk assessments
01/02/02 Vulnerability, threat, and impact assessments
01/02/03 Potential security threats (for example, all hazards, criminal activity) NEW
Task 01/03 Evaluate methods to improve the security program on a continuous basis through the use of auditing, review, and assessment
Knowledge of:
01/03/01 Cost-benefit analysis methods
01/03/02 Risk management strategies (for example, avoid, assume/accept, transfer, spread)
01/03/03 Risk mitigation techniques (for example, technology, personnel, process, facility design) NEW
01/03/04 Data collection and trend analysis techniques NEW
Task 01/04 Develop and manage external relations programs with public sector law enforcement or other external organizations to achieve security objectives
Knowledge of:
01/04/01 Roles and responsibilities of external organization and agencies
01/04/02 Methods for creating effective working relationships
01/04/03 Techniques and protocols of liaison
01/04/04 Local and national Public/Private Partnerships (example Fusion Centers) NEW
Task 01/05 Develop, implement, and manage employee security awareness programs to achieve organizational goals and objectives
Knowledge of:
01/05/01 Training methodologies
01/05/02 Communication strategies, techniques, and methods
01/05/03 Awareness program objectives and program metrics NEW
01/05/04 Elements of a security awareness program (for example, roles and responsibilities, physical risk, communication risk, privacy) NEW
Domain II: Business Principles and Practices (13%) Old Weight (11%)
Task 02/01 Develop and manage budgets and financial controls to achieve fiscal responsibility
Knowledge of:
02/01/01 Principles of management accounting, control, and audits
02/01/02 Business finance principles and financial reporting
02/01/03 Return on Investment (ROI) analysis
02/01/04 The lifecycle for budget planning purposes
Preventive and corrective
maintenance for systems
Task 02/02 Develop, implement, and manage policies, procedures, plans, and directives to achieve organizational objectives
Knowledge of:
02/02/01 Principles and techniques of policy/procedures development
02/02/02 Communication strategies, methods, and techniques
02/02/03 Training strategies, methods, and techniques
02/02/04 Cross-functional collaboration NEW
02/02/05 Relevant laws and regulations NEW
Task 02/03 Develop procedures/ techniques to measure and improve organizational productivity
Knowledge of:
02/03/01 Techniques for quantifying productivity/metrics/key performance indicators (KPI)
02/03/02 Data analysis techniques and cost-benefit analysis
02/03/03 Improvement techniques (for example, pilot programs, education and training) NEW
Task 02/04 Develop, implement, and manage security staffing processes and personnel development programs in order to achieve organizational objectives
Knowledge of:
02/04/01 Interview techniques for staffing
02/04/02 Candidate selection and evaluation techniques
02/04/03 Job analysis processes
02/04/04 Pre-employment background screening NEW
02/04/05 Principles of performance evaluations, 360 reviews, and coaching
02/04/06 Interpersonal and feedback techniques
02/04/07 Training strategies, methodologies, and resources
02/04/08 Retention strategies and methodologies NEW
02/04/09 Talent management and succession planning NEW
Task 02/05 Monitor and ensure a sound ethical climate in accordance with regulatory requirements and the organization’s directives and standards to support and promote proper business practices
Knowledge of:
02/05/01 Good governance standards
02/05/02 Guidelines for individual and corporate behavior
02/05/03 Generally accepted ethical principles
02/05/04 Confidential information protection techniques and methods
02/05/05 Legal and regulatory compliance NEW
Task 02/06 Provide advice and assistance to management and others in developing performance requirements and contractual terms for security vendors/suppliers NEW
Knowledge of:
02/06/01 Key concepts in the preparation of requests for proposals and bid reviews/evaluations NEW
02/06/02 Service Level Agreements (SLA) definition, measurement and reporting NEW
02/06/03 Contract law, indemnification, and liability insurance principles NEW
02/06/04 Monitoring processes to ensure that organizational needs and contractual requirements are being met NEW
Domain III: Investigations (10%)
Task 03/01 Identify, develop, implement, and manage investigative functions
Knowledge of:
03/01/01 Principles and techniques of policy and procedure development
03/01/02 Organizational objectives and cross-functional collaboration
03/01/03 Types of investigations (for example, incident, misconduct, compliance) NEW
03/01/04 Internal and external resources to support investigative functions
03/01/05 Report preparation for internal purposes and legal proceedings
03/01/06 Laws pertaining to developing and managing investigative programs NEW
Task 03/02 Manage or conduct the collection and preservation of evidence to support investigation actions
Knowledge of:
03/02/01 Evidence collection techniques
03/02/02 Protection/preservation of crime scene
03/02/03 Requirements of chain of custody
03/02/04 Methods for preservation of evidence
03/02/05 Laws pertaining to the collection and preservation of evidence NEW
Task 03/03 Manage or conduct surveillance processes
Knowledge of:
03/03/01 Surveillance techniques
03/03/02 Technology/equipment and personnel to conduct surveillance
03/03/03 Laws pertaining to managing surveillance processes NEW
Task 03/04 Manage and conduct investigations requiring specialized tools, techniques, and resources
Knowledge of:
03/04/01 Techniques, tools and resources related to:
- financial and fraud related crimes
- intellectual property and industrial espionage crimes
- arson and property crimes
- cybercrimes
The use of human rights codes
for cautioned statements
Task 03/05 Manage or conduct investigative interviews
Knowledge of:
03/05/01 Methods and techniques of eliciting information
03/05/02 Techniques for detecting deception
03/05/03 The nature of non-verbal communication and cultural considerations
03/05/04 Rights of interviewees NEW
03/05/05 Required components of written statements
03/05/06 Laws pertaining to managing investigative interviews NEW
Task 03/06 Provide coordination, assistance, and evidence such as documentation and testimony to support legal counsel in actual or potential criminal and/or civil proceedings NEW
Knowledge of:
03/06/01 Statutes, regulations and case law governing or affecting the security industry and the protection of people, property and information NEW
03/06/02 Criminal law and procedures NEW
03/06/03 Civil law and procedures NEW
03/06/04 Employment law (e.g., wrongful termination, discrimination and harassment) NEW
Domain IV: Personnel Security (12%)
Task 04/01 Develop, implement, and manage background investigations for hiring, promotion, or retention of individuals
Knowledge of:
04/01/01 Background investigations and personnel screening techniques
04/01/02 Quality and types of information sources
04/01/03 Screening policies and guidelines NEW
04/01/04 Laws and regulations pertaining to personnel screening NEW
Task 04/02 Develop, implement, manage, and evaluate policies, procedures, programs and methods to protect individuals in the workplace against human threats (for example, harassment, violence)
Knowledge of:
04/02/01 Protection techniques and methods
04/02/02 Threat assessment
04/02/03 Prevention, intervention and response tactics
04/02/04 Educational and awareness program design and implementation
04/02/05 Travel security program
04/02/06 Laws, government, and labor regulations regarding organizational efforts to reduce employee substance abuse NEW
Travel security programs
Task 04/03 Develop, implement, and manage executive protection programs
Knowledge of:
04/03/01 Executive protection techniques and methods
04/03/02 Risk analysis
04/03/03 Liaison and resource management techniques
04/03/04 Selection, costs, and effectiveness of proprietary and contract executive protection personnel
Domain V: Physical Security (25%)
Task 05/01 Conduct facility surveys to determine the current status of physical security
Knowledge of:
05/01/01 Security protection equipment and personnel
05/01/02 Survey techniques
05/01/03 Building plans, drawings, and schematics
05/01/04 Risk assessment techniques
05/01/05 Gap analysis NEW
Task 05/02 Select, implement, and manage physical security strategies to mitigate security risks
Knowledge of:
05/02/01 Fundamentals of security system design
05/02/02 Countermeasures
05/02/03 Budgetary projection development process
05/02/04 Bid package development and evaluation process
05/02/05 Vendor qualification and selection process
05/02/06 Final acceptance and testing procedures
05/02/07 Project management techniques
05/02/08 Cost-benefit analysis techniques
05/02/09 Labor-technology relationship NEW
Task 05/03 Assess the effectiveness of physical security measures by testing and monitoring
Knowledge of:
05/03/01 Protection personnel, technology, and processes
05/03/02 Audit and testing techniques
05/03/03 Preventive and corrective maintenance for systems NEW
Domain VI: Information Security (9%) Old Weight (8%)
Current methods used
to compromise information
Task 06/01 Conduct surveys of information asset facilities, processes, systems, and services to evaluate current status of information security program
Knowledge of:
06/01/01 Elements of an information security program, including physical security, procedural security, information systems security, employee awareness, and information destruction and recovery capabilities NEW
06/01/02 Survey techniques
06/01/03 Quantitative and qualitative risk assessments
06/01/04 Risk mitigation strategies (for example, technology, personnel, process, facility design) NEW
06/01/05 Cost-benefit analysis methods
06/01/06 Protection technology, equipment and procedures
06/01/07 Information security threats NEW
06/01/08 Building and system plans, drawings, and schematics
Current trends and techniques
for compromising information
Task 06/02 Develop and implement policies and procedures to ensure information is evaluated and protected against all forms of unauthorized/ inadvertent access, use, disclosure, modification, destruction or denial
Knowledge of:
06/02/01 Principles of management
06/02/02 Information security theory and terminology
06/02/03 Information security industry standards (e.g., ISO, PII, PCI) NEW
06/02/04 Relevant laws and regulations regarding records management, retention, legal holds and destruction practices
06/02/05 Practices to protect proprietary information and intellectual property
06/02/06 Protection measures, equipment, and techniques; including information security processes, systems for physical access, data control, management, and information destruction
Evaluate the effectiveness of the information
security program’s integrated security
controls, to include related policies,
procedures and plans, to ensure
consistency with organization strategy,
goals and objectives
Task 06/03 Develop and manage a program of integrated security controls and safeguards to ensure information asset protection including confidentiality, integrity, and availability
Knowledge of:
06/03/01 Elements of information asset protection including confidentiality, integrity, and availability, authentication, accountability, and audit ability of sensitive information and associated information technology resources, assets and investigations NEW
06/03/02 Information security theory and systems methodology
06/03/03 Multi-factor authentication techniques NEW
06/03/04 Threats and vulnerabilities assessment and mitigation
06/03/05 Ethical hacking and penetration testing techniques and practices NEW
06/03/06 Encryption and data masking techniques NEW
06/03/07 Systems integration techniques
06/03/08 Cost-benefit analysis methodology
06/03/09 Project management techniques
06/03/10 Budget development process
06/03/11 Vendor evaluation and selection process
06/03/12 Final acceptance and testing procedures, information systems, assessment, and security program documentation
06/03/13 Protection technology, investigations, and procedures
06/03/14 Training and awareness methodologies and procedures
Domain VII: Crisis Management (10%) Old Weight (8%)
Making the business case
to management
Task 07/01 Assess and prioritize threats to mitigate potential consequences of incidents
Knowledge of:
07/01/01 Threats by type, likelihood of occurrence, and consequences
07/01/02 “All hazards” approach to assessing threats NEW
07/01/03 Cost-benefit analysis
07/01/04 Mitigation strategies
07/01/05 Risk management and business impact analysis methodology
07/01/06 Business Continuity standards (e.g., ISO 22301) NEW
Task 07/02 Prepare and plan how the organization will respond to incidents
Knowledge of:
07/02/01 Resource management techniques
07/02/02 Emergency planning techniques
07/02/03 Triage and damage assessment techniques NEW
07/02/04 Communication techniques and notification protocols
07/02/05 Training and exercise techniques
07/02/06 Emergency operations center (EOC) concepts and design
07/02/07 Primary roles and duties in an incident command structure
Task 07/03 Respond to and manage an incident
Knowledge of:
07/03/01 Resource management techniques
07/03/02 EOC management principles and practices
07/03/03 Incident management systems and protocols NEW
Task 07/04 Recover from incidents by managing the recovery and resumption of operations
Knowledge of:
07/04/01 Resource management techniques
07/04/02 Short and long-term recovery strategies
07/04/03 Recovery assistance resources
07/04/04 Mitigation opportunities in the recovery process
Committee Positions
Chapter 134 thanks to Wallace Kelley of Securitas Security Services, Inc. for volunteering to take on the chair of the Young Professionals committee.
Mahalo to Joe Miller who is stepping down after several years as chair. We wish Wallace the best of luck in his new position.
Allan J. Cross Award
Congratulations to chapter member Jerry Pahukula Jr., CPP, ARVP, who is the recipient of this years Allan J. Cross Award.
For additional information regarding ASIS awards and scholarships please visit: https://www.asisonline.org/get-involved/awards--scholarships/
Chapter Elections 2016
Congratulations to our re-elected Chapter Officers announced at our December meeting by ARVP Jerry Pahukula, CPP.
Their term of office begins January 1, 2016.
Chapter Chair - Jim Frame, CPP
Vice Chair - Randy Mack, CPP
Secretary - Robert Cravalho
Treasurer - Miguel Tostado, CPP
Jerry Pahukula remains in place as our appointed ARVP.
Microchip-Enabled Credit Card May Still Be At Risk
New Microchip-Enabled Credit Cards May Still Be Vulnerable to Exploitation by Fraudsters
By October 2015, many U.S. banks will have replaced millions of traditional credit cards, which rely on data stored on magnetic strips, with new credit cards containing a microchip known as an EMV chip. While EMV cards offer enhanced security, the FBI is warning law enforcement, merchants, and the general public that these cards can still be targeted by fraudsters.
What is an EMV credit card?
The small gold chip found in many credit cards is most often referred to as an EMV chip. Cards containing this chip are known as EMV cards, as well as “chip-and-signature,” “chip-and-pin,” or “smart” cards. The name “EMV” refers to the three originators of chip-enabled cards: Europay, MasterCard, and Visa. EMV chips are now the global standard for credit card security. Unlike traditional credit cards that store data on a magnetic strip, EMV cards store card data in tiny integrated circuits and are authenticated when the cardholder inputs a PIN into a PoS terminal.
TECHNICAL DETAILS
With traditional credit cards, the magnetic strip on the back of the card contains data and personal information about the cardholder. This information is used to authenticate the card at the point of sale (PoS), before the purchase is authorized. While most EMV cards still retain the traditional magnetic strip and the cardholder’s signature on the back of the card, they offer the additional enhancement of the microchip embedded into the card. This allows merchants to verify the card’s authenticity by the cardholder’s personal identification number (PIN), which is known only to the cardholder and the issuing financial institution. In addition, EMV cards transmit transaction data between the merchant and the issuing bank with a special code that is unique to each individual transaction. This provides the cardholder greater security and makes the EMV card less vulnerable to hacking while the data is transmitted from the PoS to the issuing bank.
THREAT
Although EMV cards will provide greater security than traditional magnetic strip cards, they are still vulnerable to fraud. EMV cards can be counterfeited using stolen card data obtained from the black market. Additionally, the data on the magnetic strip of an EMV card can still be stolen if the PoS terminal is infected with data-capturing malware. Further, the EMV chip will likely not stop stolen or counterfeit credit cards from being used for online or telephone purchases where the card is not physically seen by the merchant and where the EMV chip is not used to transmit transaction data.
DEFENSE
Consumers should closely safeguard the security of their EMV cards. This includes being vigilant in handling, signing, and activating a card as soon as it arrives in the mail, reviewing credit card statements for irregularities, and promptly reporting lost or stolen credit cards to the issuing bank. When using the EMV card at a PoS terminal, consumers should use the PIN, instead of a signature, to verify the transaction. This fully utilizes the security features built within the EMV card. Consumers should also shield the keypad from bystanders when entering their card PIN.
Merchants are encouraged to require consumers to enter their PIN for each transaction, in order to verify their identity. If a consumer uses a signature, merchants should ask to also see a government-issued photo identification card to verify the cardholder’s identity.
The FBI encourages merchants to handle the EMV card and its data with the same security precautions they use for standard credit cards. Merchants handling sales over the telephone or via the Internet are encouraged to adopt additional security measures to ensure the authenticity of cards used for transactions. At a minimum, merchants should use secure servers and payment links for all Internet transactions with credit cards, and information should be encrypted, if possible, to avert hackers from compromising card information provided by consumers. Credit card information taken over the telephone should be encrypted, and any written copies of the card information should be securely disposed.
If you believe you have been a victim of credit card fraud, reach out to your local law enforcement or FBI field office, and file a complaint with the Internet Crime Complaint Center (IC3) at www.IC3.gov
Mahalo to Jerry Dolak for providing this valuable information.
Interface Information Security Conference
The Interface Information Security seminar and conference was held at the Sheraton Waikiki on September 10th and attended by several Hawaii Chapter 134 members. There were exhibits from Trend Micro, Kaspersky, Systemmetrics, Intech, AppSense, and several other info security companies. There were educational presentations, and both lunch and a cocktail reception were included in the free conference.
Six CEU points were available for participants who attended all educational sessions, and our own Chapter Chair, Jim Frame was a member of the Advisory Board. Hopefully this will become an annual event here in Honolulu.
FBI Citizen's Academy
Congratulations to chapter members Jerry Dolak and Joe Miller who graduated from the Honolulu FBI Citizen's Police Academy in June 2015. This annual program runs eight weeks and is part of the FBI Outreach program. It helps educate the public about the role of the FBI in today's world.
Weekly classes include cybercrime, terrorism, domestic spying and a chance to participate in firearms training at the FBI range. Successful completion of the course is highlighted by a graduation ceremony and dinner where course diplomas are awarded. Overall, an excellent program highly recommended for all chapter members.
Law Enforcement & Security Appreciation Banquet
The Law Enforcement & Security Appreciation Banquet Steering Committee is comprised of chapter presidents of several Hawaii based Security Associations who volunteer their time to administer program. The originating association, ASIS, started the appreciation banquet 30 years ago with the development of a process to promote, encourage and recognize excellence in the fields of Law Enforcement and Private Security, through the presentation of specific awards each year.
Any Law Enforcement agency, Private Security agency, or Security Association may submit nominations for specific service awards, or for private individual awards within the State of Hawaii connected with law enforcement or security. The program is non profit and any funds raised are used to offset the banquet costs or carried over to the next years banquet costs.
This year we celebrate our 31st year honoring the men and women of law enforcement and security who make daily sacrifices to keep our citizens and community safe.
CONGRATULATIONS TO ALL OUR 2015 AWARDEES!
2015 Seminar in Anaheim, California
The 61st annual seminar was held September 28th through October 1st at the Anaheim Convention Center.
Chapter 134 members in attendance were Jim Frame, Jerry Dolak, Jerry Pahukula, Joe Miller, Rick Osborne, Brian Ishikawa, and Ed Howard. It was good to see former Hawaii member Scott Mitchum who now resides in LA also attending. Scott sends his best wishes of aloha to all his colleagues in Hawaii.
There were great informational sessions, excellent keynote addresses by former NYC Police Commissioner Ray Kelly and retired 4 star General Michael Hayden who previously served as director of both the CIA and NSA.
The exhibit floor was the place to go for the latest in security products with a chance to get a "hands on" look at equipment and information to assist you getting the best in technology in your workplace.
There was plenty of after hours activities to keep attendees entertained with trips to the LA Angels baseball games, car museums, private estate parties and more.
Overall, a fun time spent networking with security professionals and colleagues, seeing new security products and taking advantage of the educational sessions offered at the seminar.
The 2016 seminar will be held in Orlando, Florida.

Jim Frame, CPP, Current Chapter Chairman Extraordinaire

Jerry, Dolak, CPP, Past Chapter Chairman, Asst. Regional Vice President and current newsletter editor

Joe Miller, CPP, Past Chapter Chairman, and current Webmaster
